This message will appear when the Malwarebytes web protection blocks a program or your browser from accessing an IP address range that their research has found to contain malicious content. Rather the user is greeted by an interface showing the three main features of the anti-malware package, those being detection history, the scanner, and real-time protection. System Restore enables Windows users to roll back all changes made to the OS since the latest restore point creation time. Although our software is no longer sold in Apple stores, employees that use our software and are familiar with our company have referred Mac users that are having trouble with their hard drive to either Drive Genius or Data Rescue.
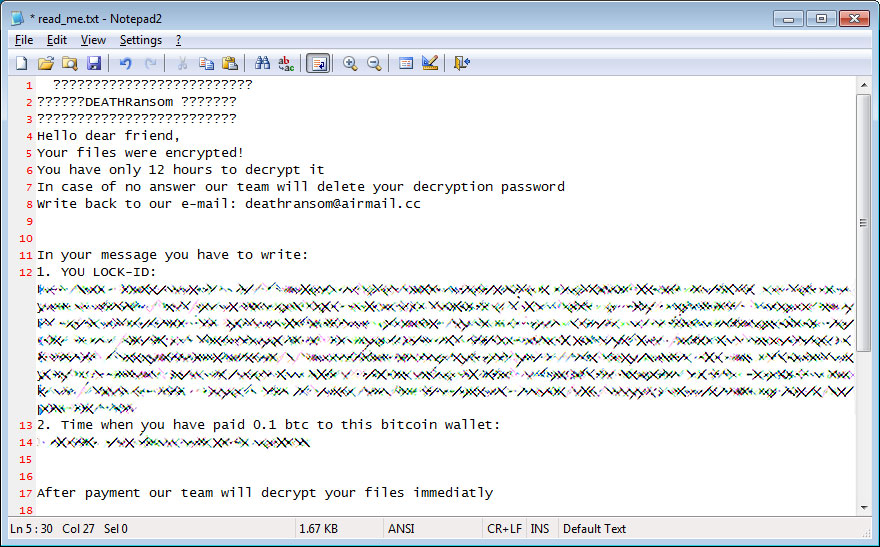
The contents oftopi files are not available until they are decrypted. Security experts don’t recommend that users reboot their computers after suffering a ransomware infection, as this could help the malware in certain circumstances. A large portion of our customers come to us for spyware and virus removal. Malwarebytes Anti-Malware and Spybot Free Edition (formerly Spybot Search & Destroy) have often found things other programs have missed. MacOS also uses a type of temporary file storage known as a cache” that helps programs run faster, and these cache files can sometimes build up if not regularly deleted.
If you can browse through directories or apps but you can’t open your regular office files, movies, photographs or emails, then you have encrypting ransomware, which is far worse. Like real-life viruses, computer viruses thrive by infecting their hosts — in this case, Macs. Spyware removal is a key component in internet security, and the removal software is referred to as ‘antispyware’. If you’re dealing with a macOS system from 10.14 Mojave onwards, you may find command line investigations hampered by macOS’s recent user protections In order to avoid those, ensure that Terminal has been added to the Full Disk Access panel in the Privacy pane.
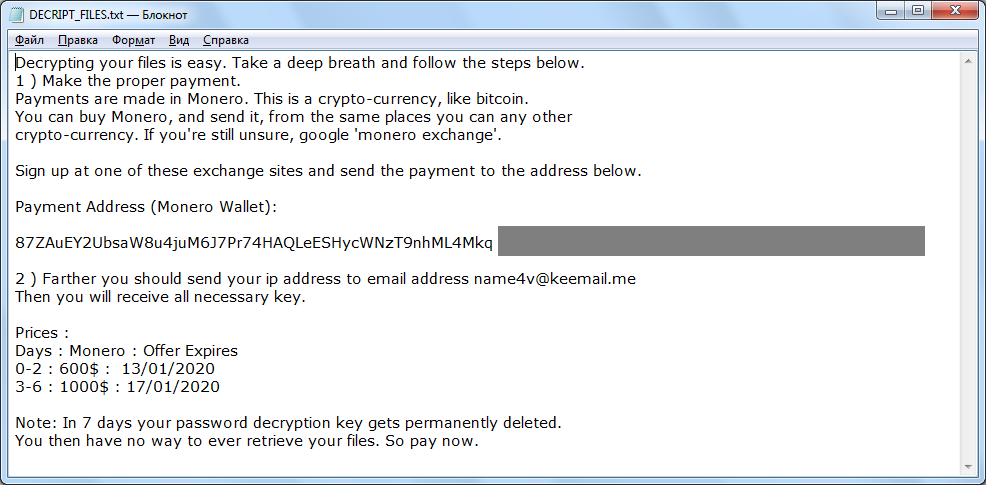
Emsisoft Decryptor for STOP Puma will allow for the decryption of files held hostage by the PUMA strain of ransomware. To use the available RAM efficiently, Mac OS X employs Virtual Memory ( VM ). This includes dynamic paging: maximizing available RAM by moving data from RAM to swap files on the startup disk and back. Set it to scan automatically or run instant checks on suspicious files. Malicious spams work by sending potential victims unsolicited Malwarebytes Anti-Malware Download emails that contain infected links or file attachments (Word file, PDF) that will download the ransomware to the defenseless victim’s computer.
If infected with ransomware, you will need to reformat your computer to ensure complete removal of means everything in your computer will be wiped out. As we’ve seen in the past couple years alone with Sony, Target, and Schnucks for example, a data breach in the network, loss of data, or malicious attacks in the form of malware can cripple a business, if not wipe it out entirely. Security awareness training will help employees spot a poisoned email that may contain a link to a site serving up ransomware.